Understanding how cyberattacks work can seem very difficult at first, but one useful way to break it down is by using the Cyber Kill Chain. Think of it like a recipe or a checklist that shows the exact steps a hacker follows to carry out an attack. Let’s go through each step in detail using simple language that’s easy to understand.
What is the Cyber Kill Chain?
The Cyber Kill Chain is a framework that divides a cyberattack into several clear steps. It was created by Lockheed Martin in 2011 and is now used by many cybersecurity professionals. Knowing these steps is like having a roadmap that shows where a hacker might try to sneak in. This understanding can help you or your organization build defenses at each point, making it much harder for an attacker to succeed.
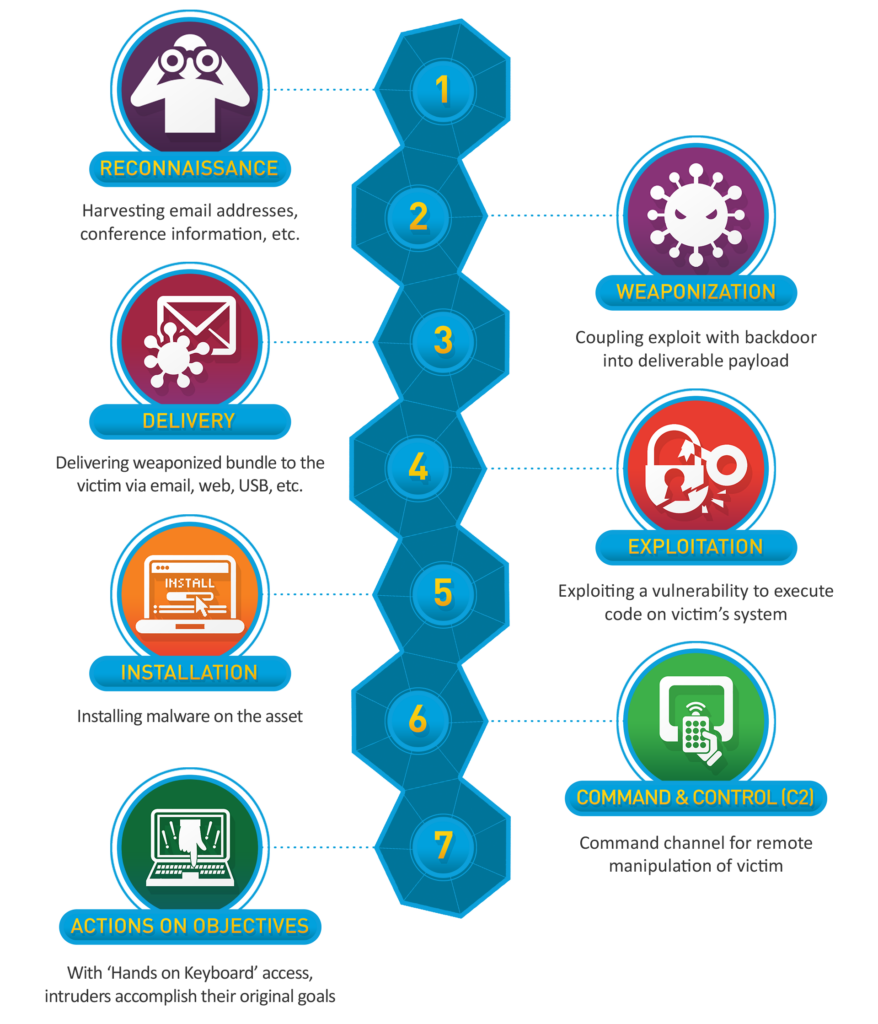
The 7 Steps of the Cyber Kill Chain in Detail
Let’s take a closer look at each step, with extra details and examples to help you understand how they work.
Reconnaissance
Reconnaissance is the first step in a hacker’s process, where they gather as much information as possible about their target, like a person, company, or computer network. During this stage, the hacker looks for details online, such as checking the company’s website, social media profiles, and public records. They also use special tools to scan the network to find out what kind of software or hardware is being used.
This step is important because it helps the hacker find weaknesses, like old software or misconfigured systems, which could be used to attack later. Reconnaissance is like a thief walking around a neighborhood, looking for houses with open windows or unlocked doors.
For example, a hacker might use a tool to check for open ports, which are like doors into a computer system, to see if the system is exposed to the internet and can be attacked.
Weaponization
Weaponization is the stage where the hacker creates the “weapon” they will use in the attack. This weapon is usually harmful software, called malware, or a trick, like a fake email designed to deceive someone. Based on the information they have gathered, the hacker targets a specific weakness in the system. They then write or modify a piece of code, such as a virus or ransomware, to take advantage of that weakness. The malware is tailored to work on that exact system, much like a locksmith making a key that fits a specific lock.
For example, if a system is using an old version of software with security flaws, the hacker can create malware to exploit those flaws.
Delivery
Delivery is the stage where the hacker sends the harmful tool, like malware, to the target. This is when the attack really begins. The hacker can use different methods to send the malware, such as phishing emails, infected websites, or even USB drives left in public places. The hacker hopes that the target will unknowingly open the email or plug in the infected USB drive.
This step is important because even the best malware is useless if it never reaches the target. It’s similar to a courier delivering a package, except the package contains something harmful. For example, a hacker might send an email that looks like it comes from a trusted source, tricking the recipient into clicking a link that downloads the malware.
Exploitation
Exploitation is when the delivered malware is activated, and this is the key moment when the hacker uses the weakness they found to get into the system. Once the malware is inside the target system, it starts running its code. The malware takes advantage of a specific vulnerability, which is a flaw or weak point in the system, to break in.
This step is important because it’s like using a special tool to unlock a door. If the vulnerability is successfully exploited, the hacker gains access.
For example, the malware might exploit a known bug in the operating system that allows it to run without the user’s permission.
Installation
After gaining access through exploitation, the hacker installs the malware on the system. This step creates a hidden entry point, allowing the hacker to return later without needing to break in again. The malware is installed in a way that is hard for the user or regular antivirus software to detect, often creating a “back door” or secret entry point.
The importance of this step is that it ensures long-term access to the system, even if the original vulnerability is fixed. For example, a hacker might install a program that runs quietly in the background, keeping the door open for future commands.
Command and Control (C2)
In this stage, the hacker sets up a communication channel with the infected system. This channel allows them to send commands and control the system remotely. The malware connects back to a server controlled by the hacker, through which they can issue instructions like stealing data or spreading the malware to other systems.
This phase is crucial because it gives the hacker power over the compromised system, like having a remote control. For example, the hacker might use this channel to make the computer send sensitive files to a remote server.
Actions on Objectives
This is the final step where the hacker achieves their main goal. The objectives can range from stealing data to disrupting services or even demanding ransom. Once the hacker has control of the system, they perform the main task, like copying important files, deleting data, or locking users out of their system. This is the end goal of the attack, where the hacker benefits from their efforts.
For instance, in a ransomware attack, this is when the hacker encrypts the user’s files and demands money to decrypt them.
Is there an eighth step in the cyber kill chain?
Some security experts believe that there should be an eighth step in the cyber kill chain called monetization. This step focuses on the hacker’s goal of making money from the attack. The hacker may ask for a ransom, demanding money by threatening to release or sell sensitive data, like personal information or company secrets.
Monetizing cyberattacks has become a bigger problem recently because of the use of cryptocurrency. Cryptocurrency makes it easier and safer for hackers to ask for and receive money, which has led to a rise in cybercriminals making money from their attacks.
Real-Life Example to Illustrate the Cyber Kill Chain Process in Detail
Understanding the Cyber Kill Chain becomes much clearer when we look at real-world examples. Here are three detailed case studies that show how each step of the kill chain was used by hackers during major cyberattacks.
WannaCry Ransomware Attack
WannaCry was one of the most widely known ransomware attacks. It spread very quickly in May 2017, affecting hundreds of thousands of computers in more than 150 countries.
Step-by-Step Details:
- Reconnaissance:
The hackers behind WannaCry first conducted reconnaissance to find vulnerable systems. They specifically searched for computers running older, unpatched versions of the Windows operating system, which had known vulnerabilities. They used tools to scan for open ports and security weaknesses, and the vulnerability they targeted was known as EternalBlue, a flaw in Microsoft’s implementation of the Server Message Block (SMB) protocol. - Weaponization:
After identifying vulnerable systems, the attackers weaponized the exploit. They created the WannaCry ransomware, which was specifically designed to exploit the EternalBlue vulnerability. WannaCry used this flaw to spread across networks and encrypt files on infected computers. The ransomware also used another exploit called DoublePulsar, which allowed it to gain access to systems without detection. - Delivery:
The malware was delivered mainly through a network attack rather than traditional methods like phishing emails. Although some variants spread through phishing, WannaCry’s key strength was its ability to move laterally within networks, jumping from one vulnerable system to another without human involvement. This means that once a single computer was infected, the malware could spread across an entire organization automatically. - Exploitation:
Once the WannaCry ransomware reached a vulnerable system, it exploited the EternalBlue vulnerability. After gaining access, it immediately began encrypting files, locking users out of their documents, images, and other critical data. This disruption rendered essential files and information inaccessible to the user. The system was left inoperable unless the ransom was paid. - Installation:
After exploiting the vulnerability, WannaCry ensured that it could remain on the infected system by installing itself in the background. Even if its initial delivery methods were blocked or detected, the ransomware stayed hidden and maintained access to the system. This step guaranteed that the attacker could maintain control over the infected machine and could continue executing commands without the user’s knowledge. - Command and Control (C2):
While WannaCry didn’t use the most sophisticated Command and Control (C2) channels seen in other cyberattacks, it still communicated with remote servers. This allowed the malware to receive updates and send back information about which systems had been infected. The attackers could track the attack’s progress and adjust their strategy based on which systems were affected, helping them to know that the attack was working as planned. - Actions on Objectives:
In the final step, the WannaCry ransomware encrypted the files on the infected computers and displayed a ransom note. The attackers demanded payment, usually in Bitcoin, in exchange for a decryption key that would unlock the encrypted files. The ransom typically ranged from $300 to $600 worth of Bitcoin. Organizations and individuals faced a difficult choice: pay the ransom to recover their data or risk losing it forever.
Target Data Breach (2013)
The Target data breach of 2013 is one of the biggest and most well-known retail security failures in history. During the busy holiday season, hackers gained access to Target’s network and stole credit and debit card information from millions of customers. This breach compromised sensitive payment data, affecting millions of shoppers and making it a highly impactful cyberattack in the retail industry.
Step-by-Step Details:
- Reconnaissance:
The hackers started by researching Target’s network and connections to its third-party vendors. They found a small vendor—a company that provided services like heating and air conditioning—that had weak security. The vendor’s system was not properly protected, and it acted as an easy entry point into Target’s larger network. This method of attacking through a vendor with weaker security is a form of supply chain attack, where the hackers used the vendor’s network access to infiltrate Target. - Weaponization:
Once inside, the attackers created custom malware designed specifically for Target’s Point-of-Sale (POS) systems. The malware was built to capture sensitive payment card data, such as credit card numbers and security codes, whenever a customer made a purchase at Target stores. The hackers knew that if they could install the malware on the POS systems, they would be able to steal payment information from millions of customers across multiple locations. - Delivery:
The malware was introduced into Target’s network through the compromised vendor’s system. Since the vendor already had legitimate access to Target’s network for maintenance purposes, it was easier for the malware to enter undetected. By leveraging the vendor’s access, the hackers were able to deliver the malware into Target’s systems without raising alarms, making this delivery method highly stealthy. - Exploitation:
Once inside Target’s network, the malware exploited vulnerabilities in the POS systems. The malware ran quietly in the background, collecting data from every transaction that was processed at Target’s stores. It captured credit card numbers, expiration dates, and security codes from customers who made purchases. - Installation:
The malware was installed on multiple POS systems in many of Target’s stores. This ensured that the malware could collect a large amount of data from numerous transactions over time. The malware ran silently and was designed to remain hidden from both employees and some security systems, making it harder to detect during routine checks. - Command and Control (C2):
The attackers used a remote channel to maintain control over the infected systems. This allowed them to update the malware if necessary and collect the stolen payment data continuously. By using this command-and-control channel, the hackers were able to manage the malware remotely and make sure the theft of data continued uninterrupted. - Actions on Objectives:
The primary goal of the attackers was to steal payment card data. Once the data was collected, the hackers transferred it to their own servers. They then either used the stolen information to make fraudulent purchases or sold it on the black market to other criminals.
How Can You Protect Yourself?
Start by keeping an eye out for early signs of trouble. Use security software to track anything unusual, like failed login attempts or strange emails that look off. It’s a good idea to trust your instincts – if something seems weird, it’s worth looking into.
Keeping your software updated is another easy way to protect yourself. Updates may seem annoying, but they fix weaknesses that hackers like to exploit. So, taking the time to update your systems can make a huge difference in preventing attacks.
Learning how to recognize threats is essential. Phishing emails, fake links, and sketchy attachments are common ways hackers try to trick you into giving up personal information. By educating yourself and others around you, you can avoid falling for these tricks. Always be cautious when clicking on links, especially from unknown sources.
Strong passwords and two-factor authentication (2FA) are like the lock and key to your digital world. They make it much harder for anyone to break into your accounts. Use long, unique passwords for each account, and enable 2FA whenever possible. It’s an extra step, but it’s worth it for the added security.
Don’t forget to back up your data regularly. Having backups means that even if something goes wrong, you won’t lose everything. It’s always better to be safe than sorry when it comes to your important files and memories.
If you’re in charge of a network, consider segmenting it. Dividing your network into smaller parts can limit the damage if one area is breached. It’s like putting up walls to protect different rooms in your house – if one gets broken into, the others stay safe.
Lastly, always have an emergency plan. Know what to do if you think you’ve been hacked – whether it’s disconnecting from the internet or reaching out to a cybersecurity expert. Having a plan in place can help you act quickly and prevent things from getting worse.
Final Thoughts
The Cyber Kill Chain helps us understand the complete process of a cyberattack, from the very first scan of a target to the final moment when a hacker achieves their goal. By breaking the attack into clear, manageable steps, it becomes easier to spot where you might be vulnerable and take action to stop an attack in its tracks.
Remember, cybersecurity is not about a single solution but about creating layers of protection. By staying informed, keeping your systems updated, and following safe online practices, you can greatly reduce the risk of an attack. I hope this detailed guide has given you a clear and engaging understanding of the Cyber Kill Chain. Stay safe, stay smart, and keep learning about how to protect your digital world.
If you’re interested in learning more about how to prevent from cyberattacks, read this.










I’m not sure why but this blog is loading extremely slow for me.
Is anyone else having this problem or is it a issue on my end?
I’ll check back later on and see if the problem still exists.